Message from the Executive Director: I Was Hacked! Lessons Learned
GBA Executive Director Joel Carson
On Wednesday, July 17, I received a call from a GBA Board Member asking if I was trying to send him a proposal. While this seemed suspicious, I just told him it must be a phishing effort and asked him to disregard the email.
if I was trying to send him a proposal. While this seemed suspicious, I just told him it must be a phishing effort and asked him to disregard the email.
That was the start of an onslaught of emails, text messages, and phone calls from friends and colleagues from across North America. It quickly became apparent that my Microsoft Outlook account had been hacked and I became very concerned, very quickly. I thought about worst case scenarios and started sweating.
Here are the steps I took to overcome this significant issue.
SECURE ACCOUNT
I quickly contacted GBA’s IT consultant who thankfully is always quick to respond, even though today he was in an important meeting. He stepped out of his meeting and immediately started working with me to resolve the issue and it was not simple. It was determined that the hacker accessed my email server through my Google account and was sending out notices asking my contacts to open a proposal. Additionally, when my contacts responded by email asking if the proposal request was legitimate, the hacker responded giving a false sense of security! This is a new and sophisticated approach to hacking that I had not heard of but something we should all be aware of now.
We tried to reset my Microsoft password but it was challenging because my authenticator app had been compromised as well. After clearing select apps and setting up my email account, the issue was resolved, resecuring my account and updating my authenticator. Although I felt some relief, the work was not done.
RESPOND TO INQUIRIES
I started responding to emails and text messages about this issue. In some cases, the messages were simply to let me know something was suspicious and in other cases my contacts were asking me to send the proposal in different formats as they had followed the hacker’s instructions, provided their account information, and still could not see my proposal.
PROACTIVELY COMMUNICATE
I also asked our IT consultant for a list of all the emails that had been sent from my account since the previous day. I felt it important to let everyone know about this issue so I sent an email to each of them. I apologized, explained the situation, confirmed we take cybersecurity seriously, and provided suggestions to manage the risk.
I received numerous email responses which helped ease the stress. Our members are compassionate and supportive.
LESSONS LEARNED
Consistent with our members Case Histories, I compiled a list of lessons I learned during the day.
1. If there is an issue with your computer or suspect it has been compromised, don’t hesitate. Contact your IT support immediately and let your colleagues know.
2. If you receive a suspicious email do not open it.
3. If you think an email is suspicious but need to double-check, don’t send an email on the same format asking if it is legitimate. Call or text the person. It is important to use a different communication method to verify legitimacy.
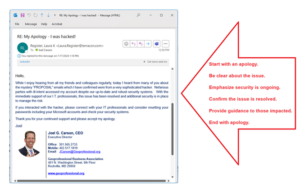
4. When you have an issue, let anyone that could be impacted know. Start with an apology, be clear about the issue, confirm the issue is resolved, provide suggestions on ways to manage risk, and end with an apology. Transparency is critical.
5. GBA Members and our business partners are awesome. They are understanding, compassionate, and supportive. I already knew this, but the points were emphasized on this day.
CLOSING
One of the things I most appreciate about GBA is the mutual support of our members through good times and through challenging times. I see this in Committee Meetings, Peer Groups, and regular communication among our members. I witnessed this firsthand. Another thing I appreciate about GBA members is our willingness to share experiences with each other so we can all learn together and elevate our profession together. In part, I was prompted to prepare this lesson learned in response to the sharing I observe each day as Director and this is why GBA Case Histories are so important.
If you have other best practices to share about computer security or technology in general, please let me know. I appreciate your support and willingness to elevate our profession.